Cheating Methods
Learn about game cheating methods
The below content has been written to be simple and to the point. It is not meant to be a full blown guide with many details on game cheating methods.
With that being said, please read below if you are interested to learn more.
Common Methods
Most common cheating methods include process injection, memory manipulation, network manipulation, MACRO software usage, bots, trainers and more.
These are generally tried and used by day to day gamers and newbie cheaters.
Process Injection
If you search "what is process injection" you will find many explanations and articles. However, you might not understand anything from them.
For this reason, we will explain in simple terms so you can understand what "process injection" is.
What is a process?
Every appplication/software that runs inside your PC is called a "process". You can view your "process list" inside your Task Manager (CTRL+ALT+DEL). A game running in your PC is also a "process".
Example of Task Manager
What is process injection?
When you read "injection" do not think of a needle and syringe. 😀
The idea of "process injection" means that a cheater can insert arbitrary executable code into the game "process" while it runs to alter the gameplay.
This method is used primarily by malware and virus authors to infect your PC and steal your data. However game hackers/cheaters adopted this technique to achieve their goal of cheating.
Sadly this is also used by third party like game overlays, live streaming software, password managers and more.
Example Process Injection
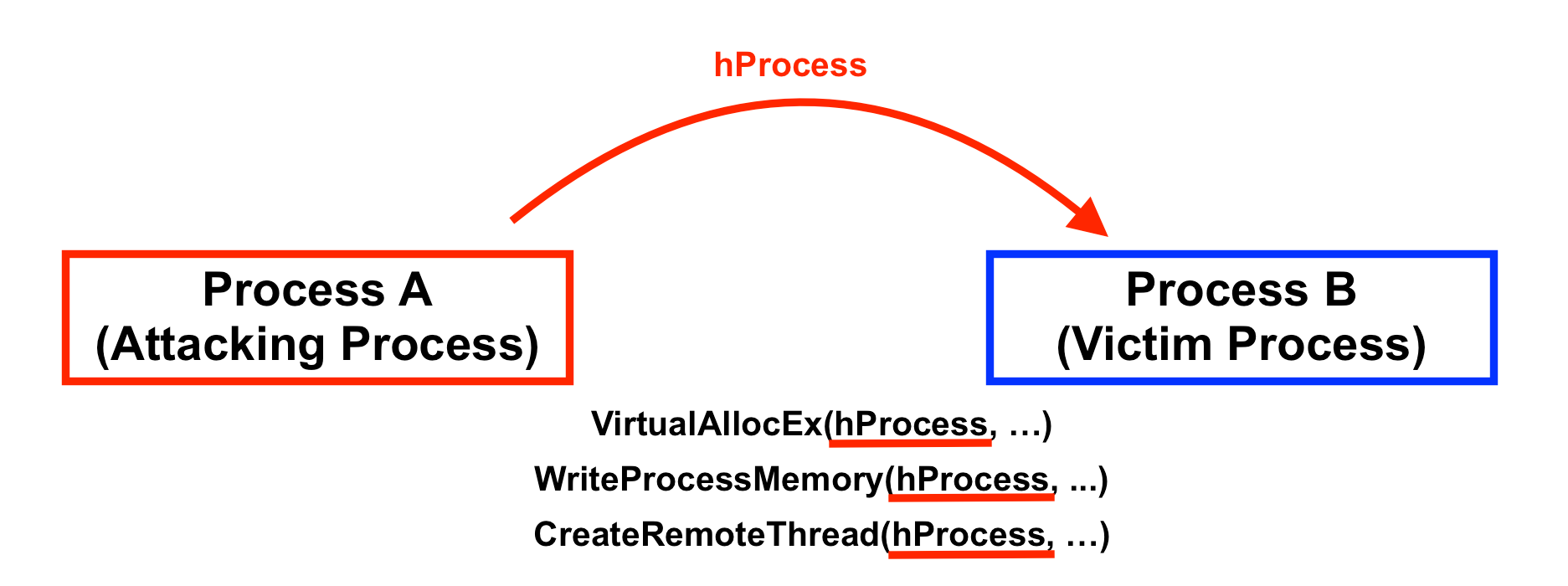
How is process injection done?
Unfortunately there are way too many methods to achieve "process injection" and because of this reason we will not enlist them here.
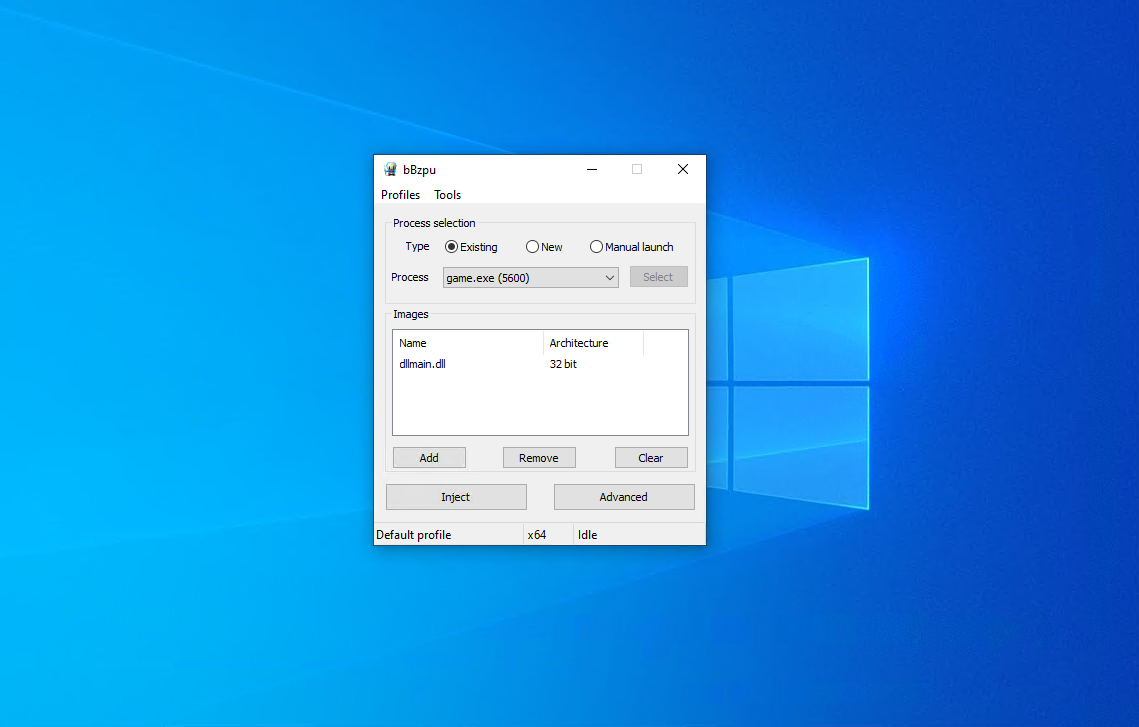
Cheaters generally use software like Cheat Engine, GH Injector, ExtremeInjector, Xenos and other custom made ones to "inject" a game process with a DLL.
Example Process Injector Software
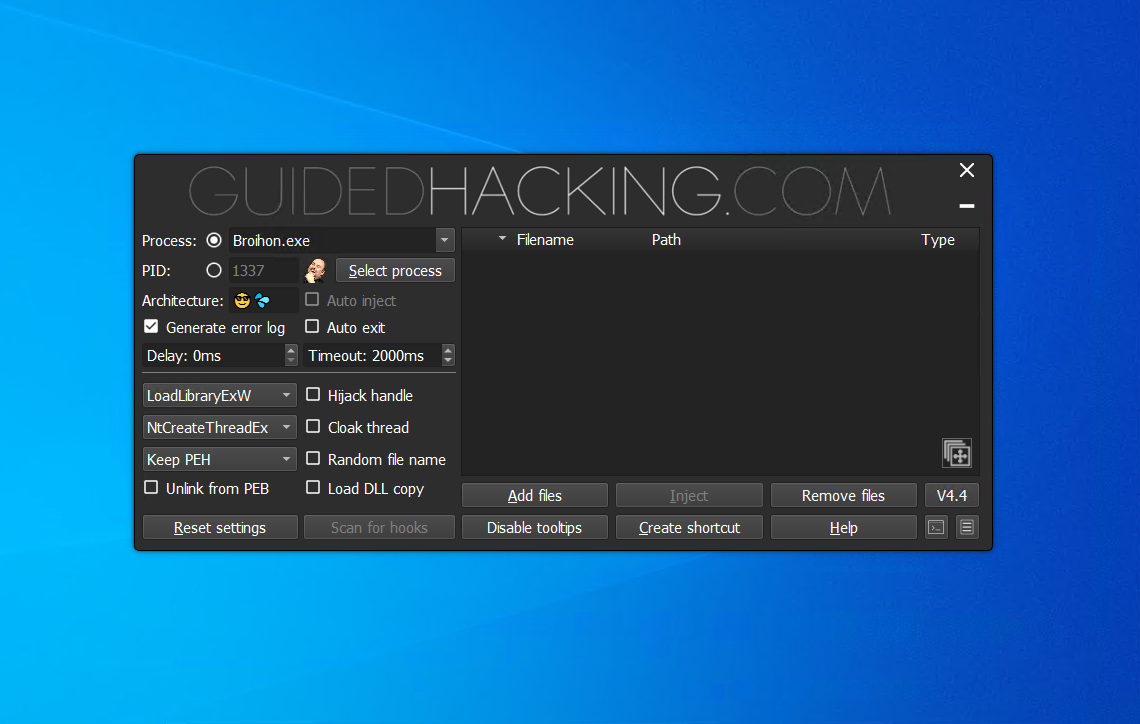
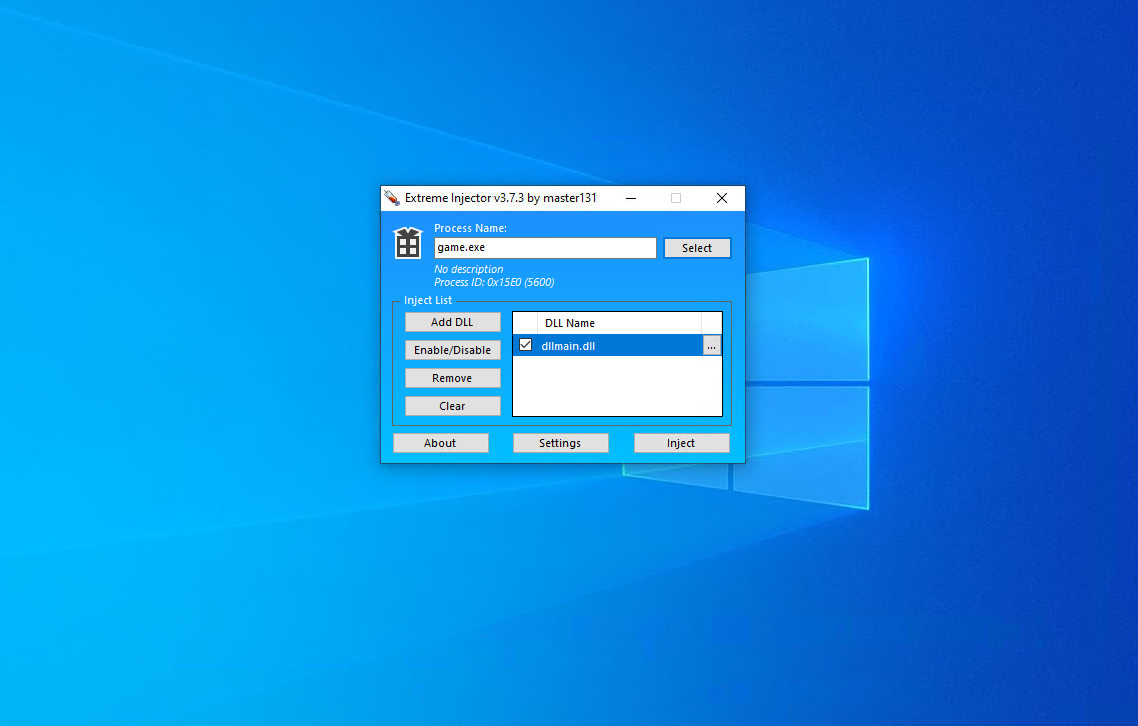
Memory Manipulation
This method is the most common way of cheating, a method that is being used day to day across many different games.
Once a cheater has access to the game memory cheating begins. This is achieved by editing certaing memory information like Health, Speed, or drawing stuff onto the game screen. The list of things that can be achieved is overwhelming.
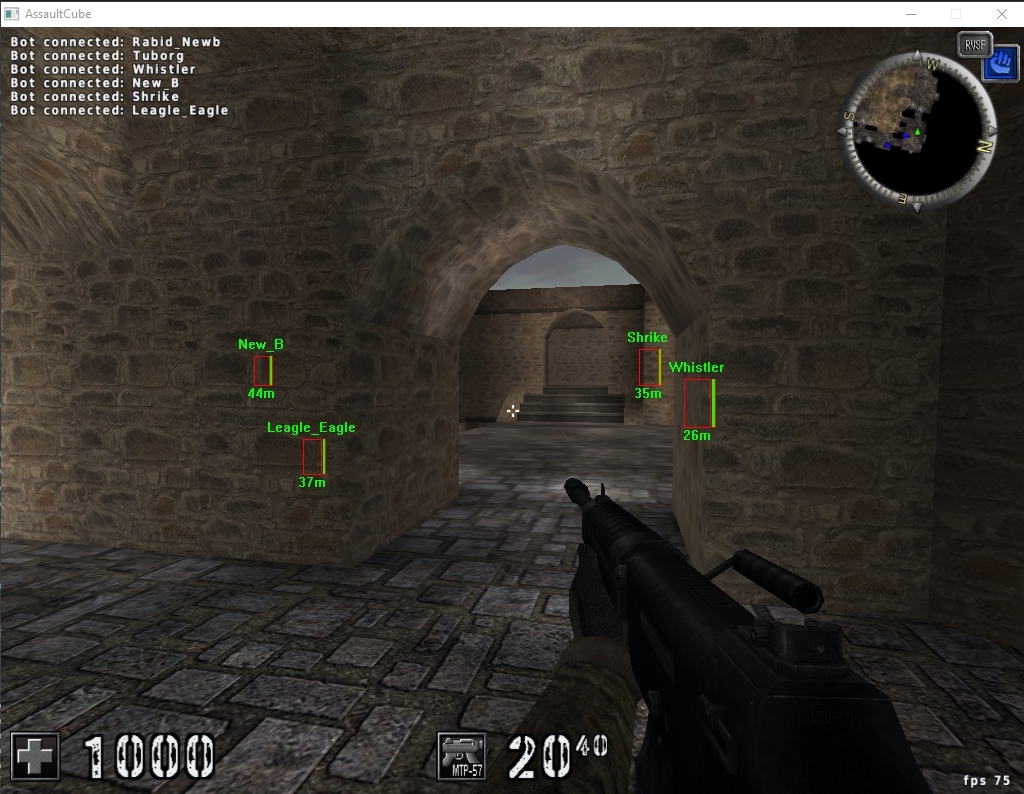
In multiplayer games cheaters generally create "ESP" (Extra Sensory Perception) to see objects, NPCs or players through walls and terrains.
Example of ESP (from guidedhacking.com)
Network Manipulation
As you can imagine, when you are playing multiplayer games there is network traffic being exchanged constantly (both ways).
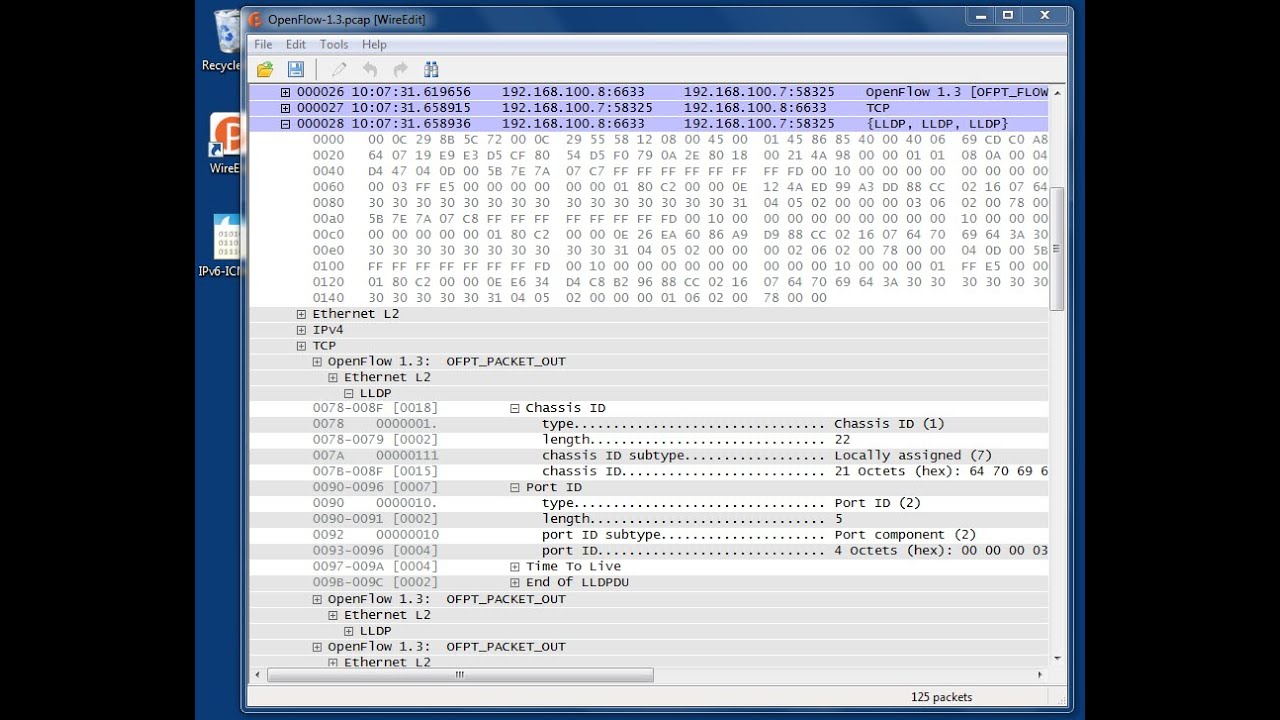
Cheaters intercept this traffic and alter its information to achieve different benefits like duplicating items, speed hacking, automatic loot of items, teleportation and much more.
Unfortunately there are many legitimate software that cheaters can use to do this, as well as specifically created software for cheating.
Example of Network Manipulation
MACRO Software
Another very common and very popular method of cheating. This is used across many different games (online and offline) to aid game cheating.
Most game cheaters will claim that using MACRO software is not cheating. Imagine someone being to automatically press the healing potion every 5 milliseconds when playing an MMORPG game.
Can you as a human press potions every 5 milliseconds?...
What is MACRO?
A macro is an automated input sequence that imitates keystrokes or mouse actions. In computer science, MACRO is a rule or pattern that specifies how a certain input should be mapped to a replacement output.
MACROs are programs used to automate frequently used processes or tasks in Excel. A macro records operations and re-uses the sequence of mouse actions or keystrokes of anything you can do in Excel with keystrokes or a mouse.
The original intention of MACROs has been adapted by game cheaters for their own purpose.
How is MACRO used?
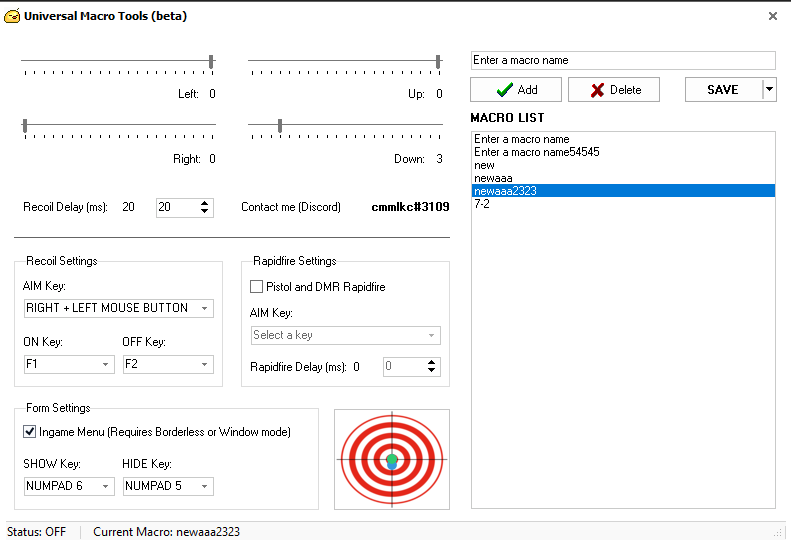
This type of software can be used either by recording keystrokes or actions, either by pre-setting certain keys or mouse buttons to be pressed automatically.
Game cheaters will use scripts and custom made software to obtain automatic keypresses.
Unfortunately there are also hardware sets that be bought which are shipped with specific software for MACRO.
Example of MACRO Software
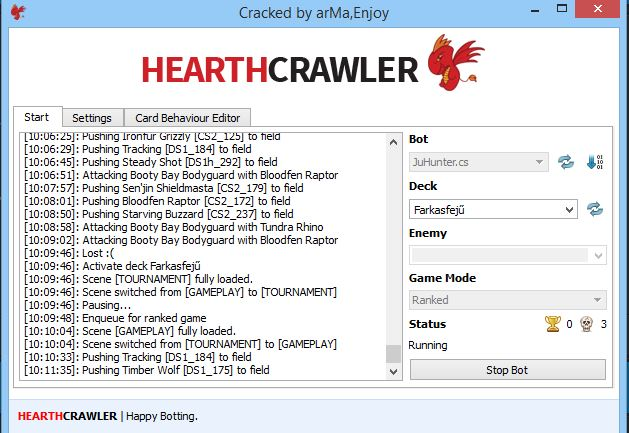
Bots/Trainers
This is yet another very popular method of game cheating. Using bots and trainers is one of the oldest methods of game cheating.
Generally bots are used for farming and automating others tasks like accepting parties, completing quests and missions and more. Trainers are rather used to overwrite game memory with specific values like infinite health and more.
What are Bots?
In video games, a bot is a type of artificial intelligence (AI)–based expert system software that plays a video game in the place of a human.
What are Trainers?
Game trainers are software made to modify memory of a game thereby modifying its behavior using addresses and values, in order to allow cheating.
Examples of Bots
Advanced Methods
More advanced game cheating methods include abusing third party software, abusing operating system and its built in software, creating custom kernel drivers and more.
These are created by expert game hackers that have extensive programming and security knowledge. Secret groups exist that do nothing else everyday besides trying to cheat and abuse software.
Abusing Software
Rather than trying to modifying the game itself, game cheaters will abuse third party software that already has legitimate access to the game. A perfect example are game overlays, which are abused all the time as a "pipe" to the actual game process.
The extent of abusing legitimate third party software is beyond your imagination. Cheaters will abuse anything they can find suitable not just overlays, but also streaming software, antivirus software and more.
Abusing System
Same methodology as above, but much more dangerous and effective. Game cheaters will alter legitimite system components that help the game to run in order to achieve cheating.
This method is one of the preffered ways of cheating since it is extremely hard to identify this. Afterall, its the "system" modifying the game is it not? 😀
Custom Kernel Drivers
Professional game cheaters will write their own kernel drivers to bypass every prevention of cheating in place. This makes them virtually "invisible" from anticheat software.
This is the preffered method of cheating nowadays, as it offers unlimited access throughout the system. Cheaters can alter anything not just the game, which gives them almost 100% success rate all the time.
Other Methods
There are plenty other methods to cheat inside a game besides the ones specified here. We only specified a few methods so you can understand what cheaters are capable of doing.